Designed to teach what Zero Trust means, how vendors approach it, and how to start building a strategy for your organization.
Learn the Essentials of Zero Trust and Identity
One of the most common topics we we encounter as a cybersecurity consulting firm is Zero Trust. Organizations want to first fully understand it, and then adopt a process to apply it to their unique needs.
This free workshop is designed to help you understand how to determine what Zero Trust really means and the best practical approaches to develop an IAM + ZT strategy. From its history and evolution to building blocks and architecture.

The Fundamentals
The entire framework is much bigger than “Never Trust, Always Verify.” We’ll discuss other areas to consider.
Common Obstacles
Common business and IT obstacles, along with recommended approaches to overcome them.
Building Blocks
Five building blocks that ZT products and approaches fall into, and how you can address each.
Understanding Zero Trust and how IAM fits within it
Start to answer the key Zero Trust and IAM questions: In order to create a Zero Trust strategy and reduce risk, you have to understand how to approach it within your organization. Since Identity and Access Management is central to achieving ZT, you also need to also understand the Identity ecosystem. This workshop will help to get you there.
⦿ The origin and history of Zero Trust
⦿ The fundamentals beyond “…always verify”
⦿ Common business and IT challenges
⦿ Separating vendor hype – why that’s important
⦿ ZT Evolution – from Networks to the Solarwinds hack
⦿ Five building blocks you can use to drive your ZT efforts
⦿ Zero Trust Architecture overview
⦿ IAM overview in context of ZT
⦿ The services and tools that make up IAM
⦿ How Maturity Models, Product Comparison exercises, roadmaps, and other deliverables can help build a solid IAM program
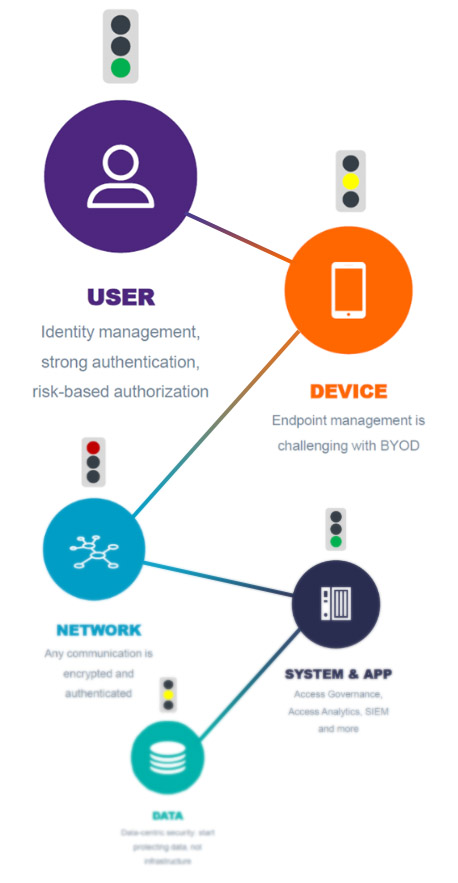
Workshop Topic Highlights
Zero Trust
Origin & Evolution
We’ll discuss the origin of Zero Trust, how and why it evolved, and how that affects your approach to it.
Zero Trust & IAM 101
(IGA? CIAM? AM? DAG?)
The key components of a Zero Trust strategy, and how ZT fits within an IAM program.
Zero Trust Architecture
There are many components that must be considered when determining the overall approach to ZT.
ZT Building Blocks
We’ll breakdown five building blocks that ZT products and approaches fall into, and discuss how you can address each.
Maturity Scoring
You’ll learn about how the IP maturity model can help prioritization and roadmapping.
The Gartner Magic Quadrants
Just because a vendor is a “leader” doesn’t mean they’re right for your use case.
Next Steps – Developing a ZT Identity Strategy & Roadmap
Learn how to use the information from the workshop to better understand where your company stands with Zero Trust and IAM. We’ll discuss steps you can take to move forward and build a solid roadmap and strategy.
Getting Started
By the end of the workshop, you will be able to clearly articulate and understand the key Zero Trust principles, how they interact within the larger IAM ecosystem, and how to approach a strategy development project. You’ll also understand how to make informed decisions moving forward.
The easiest way to get started is to have a short conversation with one of our experts. They have years of experience helping organizations get their IAM program right – from early education like this workshop, to implementation and support. They’ll answer any questions you have and get you scheduled for a workshop if that makes sense.
Just click here or use this form to schedule a short conversation.
